26. April 2024 By Marcel Erfurth
Cybercrime of tomorrow: Trends and dangers of future cyberthreats
Hektor Nagel, CFO of a medium-sized company, switches on his laptop and checks his e-mails as he does every morning. But this time everything is different. As soon as he opens his inbox, he realises that he is not receiving a manageable number of emails as usual. His inbox is full to the brim with emails from various press offices of major German DAX companies. But what has happened?
We are living in troubled times. National and international conflicts threaten our world. Economic and humanitarian crises are unfortunately not uncommon. In the midst of these problems, however, we face completely different challenges. Cybercrime is no longer just a field for hobby hackers or petty criminals. The threat landscape has expanded to include organised and structured groups. These are fully or partially financed and controlled by states. But what trends and dangers await us in the future? And how can companies effectively protect themselves against these emerging threats? I would like to explore these questions in my blog post and highlight some trends.
The Microsoft Digital Defence Report 2023
Let's take a look at the Microsoft Digital Defense Report 2023, which is published by Microsoft every autumn and represents an annual report on the current digital security situation. Microsoft's entire past financial year is analysed and currently covers the period from July 2022 to June 2023. For this blog post, all relevant page references refer to the current Cybercrime Situation Report (MDDR) Ch2 | Microsoft Security Insider.
This report not only contains marketing-relevant aspects that highlight the protective function of the Microsoft Defender Suite in particular. Various statistics are also collected and clearly presented. Microsoft also provides an "Executive Summary" for a quick overview. This briefly summarises the most important information at C-level.
Trends in modern cybercrime
One of the biggest threats in the modern business world is the unauthorised outflow of data and information. In the event of a successful attack (e.g. by ransomware), the data is not only cryptographically encrypted, but in 16 per cent of cases the data is smuggled out of the company. In 13 per cent of ransomware attacks, the goal is even exclusively the exfiltration of data.
The data collected by Microsoft since November 2022 also shows a sharp increase in potential exfiltration attacks. One of the reasons for this is the increasing use of infostealers, which use a malware-as-a-service model to sell an environment in which the main objective is the exfiltration of information by malware and the processing of this data.
It is well known that phishing is still one of the most widespread methods of attack. The fact that there are also new trends in this area, such as URL redirect attacks, in which URL shorteners are used to shorten and disguise the original phishing link, represents a new dimension.
Another trend can be observed in the area of identity theft. According to Microsoft, attacks on identities have increased sharply in the last year: an average of 4,000 password attacks per second last year. In April 2023, there were already 11,000 password attacks.
The use of multi-factor authentication is generally recommended as a defence against password attacks. But there are impressive dangers here too. So-called token replay attacks, for example, attempt to legitimise unauthorised access via classic attack scenarios such as phishing or malware by capturing authentication tokens. This type of attack has doubled to an average of 11 attacks per 100,000 users. However, it currently only accounts for three per cent of all identity attacks.
DDoS attacks are another classic form of attack. Even though they have been around for a long time, they have recently experienced a real renaissance. For example, there are DDoS-for-hire platforms, i.e. paid platforms that can be used to initiate an attack on a service. The trend is on the rise, with 20 per cent of new providers having been added in the last year alone. The growth of such botnets must be compensated for with capacities from the cloud. Unfortunately, this is also being misused for precisely these purposes. Although Microsoft found that only 15 per cent of attacks were carried out via hijacked European cloud resources, a further increase cannot be ruled out.
IT should fix it
"What's going on here?" asks Hektor Nagel in a panic as he approaches his colleagues in IT. Many puzzled faces look at him. He throws the laptop onto the desk of a colleague at the helpdesk. But then someone shouts from the next room: "Is that you, Mr Nagel?" The CIO approaches him and explains that there has been a cyberattack on the company since 03:32 yesterday morning. He asks Mr Nagel if he can remember opening a file called "VersicherungsPolicie24.pdf" about three weeks ago.
Future dangers
There will be further dangers in the future. The attack vectors are increasingly shifting to critical areas. For example, it was found that 41 per cent of all threat notifications sent by Microsoft to online service customers were sent to companies in the critical infrastructure sector (KRITIS).
In addition, there is a clear spread of locally definable targets and various industries:
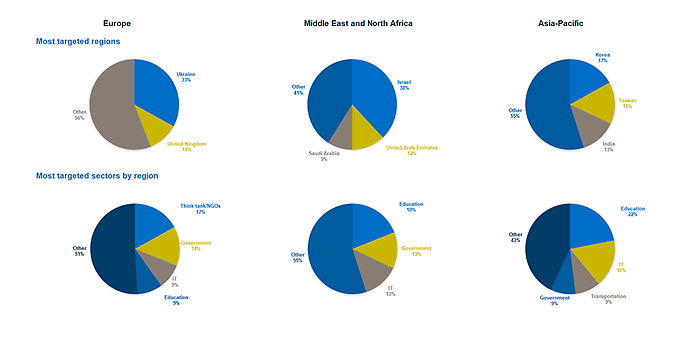
There are both political and monetary reasons for this focus.
The fact that 75 per cent of all eligible voters living in democratic countries will be going to the polls in the next eighteen months may bring in completely different motivations.
In addition, modern attacks are possible through the use of artificial intelligence. Attacks on Internet of Things devices, 78 per cent of which have known vulnerabilities and 46 per cent of which cannot be patched, will also become a higher priority in the future.
25 per cent of all operational technology devices run on operating systems that are no longer supported. The risk of software supply chain attacks, i.e. attacks that exploit known vulnerabilities in widely used software libraries, has increased by 742 per cent since 2019. More than 490 million customers are already affected. Another development to keep an eye on.
What has happened?
To unravel our little cybercrime story, we need to go back a few days: Mr Nagel had problems opening business-related PDF files, as he often does. To get help, he handed in his laptop to the company helpdesk. He enclosed a piece of paper on which the login details of his Windows user were noted. The IT trainee was handed the nice piece of hardware. He was given the task of reinstalling the PDF reader used and testing its functionality extensively.
The installation went without any further problems. During the functional test, the trainee wanted to imitate Mr Nagel's way of working as closely as possible and decided to open a PDF file that he had recently received in his email inbox. However, the file with the name "VersicherungsPolicie24.pdf" turned out to be malware. This demanded Mr Nagel's access data via an input window, which the trainee unfortunately entered negligently. This enabled remote access to Mr Nagel's laptop and his identity could be stolen, misused for various purposes and compromised.
Conclusion
This blog post has shown which threats are becoming increasingly relevant for companies today. This was illustrated using a specific example. But how can a company effectively protect itself against these threats? In addition to hardening the existing infrastructure or using up-to-date virus protection, there are other areas that a company needs to look at. Are the company's own approaches compatible with the emerging threat situation? Is a holistic security model being pursued? Are there sufficient monitoring measures in place? How does threat management work? Are there up-to-date risk and emergency plans? Are there systems in place for managing security incidents? How are identities and authorisations handled? Is there a training concept and regular awareness training?
The number of questions seems unmanageable. In the madness of everyday life, this challenge can also seem almost insurmountable. This is where qualified advice can help. This is what adesso can offer with its Microsoft Security Competence Centre.
The Competence Centre is made up of experts who are always up to date with the latest security developments relating to NIS2, GenAI and Copilot security and Zero Trust with Microsoft.
The topic of cyber security is more important than ever. Trends are developing rapidly with new approaches and the use of AI. The expected consequences of a security incident are higher than ever before. Microsoft puts the cost of cybercrime at 10.5 trillion US dollars in 2025, and with penalties such as those provided for in the GDPR or NIS2, attacks can cause significant damage not only to companies but also to executives. Start on the path to a secure future with us today!
Would you like to find out more about exciting topics from the adesso world? Then take a look at our previous blog posts.
Microsoft Security Webinar
Discover the latest strategies to strengthen your organisation's security in the digital age! Don't miss this opportunity to take your security strategy to the next level. Secure your place and register today!

